- Workspace Key & Secret → Used to authenticate requests from Backend SDKs.
- API Keys → Used to authenticate REST APIs as
Bearer <API_KEY>. - Public Key & Signing Key → Used to authenticate Client SDKs (with enhanced security options).
All keys and secrets are unique per workspace. This is done to keep your testing and production workspace separate and safeguards against accidentally sending wrong notification to your production users during testing.
1. Authenticating Backend SDKs
Backend SDKs are authenticated using a Workspace Key and Workspace Secret. To find these credentials:- Go to SuprSend Dashboard → Developers → API Keys.
- The Workspace Key and Secret for the selected workspace are shown at the top.
2. Authenticating REST API Requests
REST API requests are authenticated using API Keys. Pass the API Key in theAuthorization header with Bearer scheme:
- Navigate to Dashboard → Developers → API Keys.
- Click Generate API Key.
- Provide a name and select Create and Save.
- Copy the API Key and store it securely — it will be shown only once at generation.
3. Authenticating Client-side SDKs
Client SDKs (Web/Mobile) use Public Keys for authentication. You can manage these in Dashboard → Developers → API Keys → Public Keys.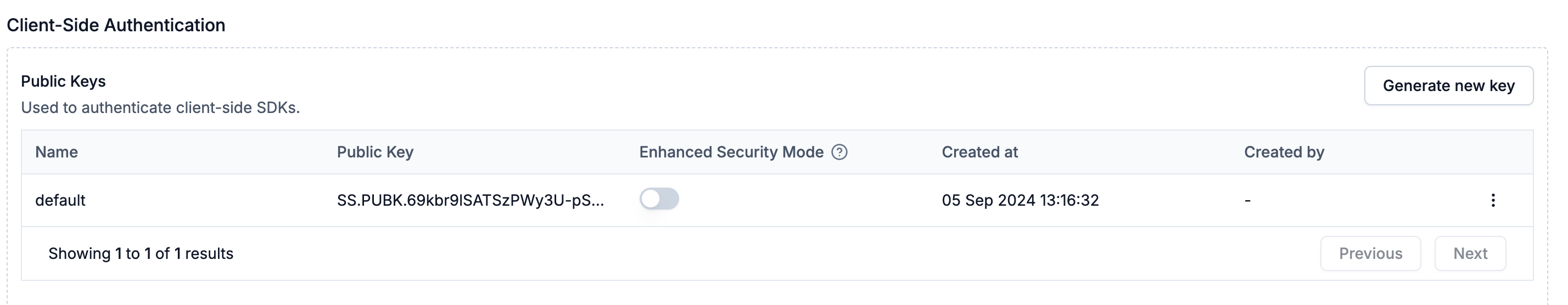
📘 Some legacy mobile SDKs may still use Workspace Key/Secret. These are being phased out.
Enhanced Security Mode with signed User Token
When enhanced security mode is on, user level authentication is performed for all requests. This is recommended for Production workspaces. All requests will be rejected by SuprSend if enhanced security mode is on and signed user token is not provided. This signed user token should be generated by your backend application and should be passed to your client.Generate Signing Key
You can generate Signing key from SuprSend Dashboard (below Public Keys section in API Keys page).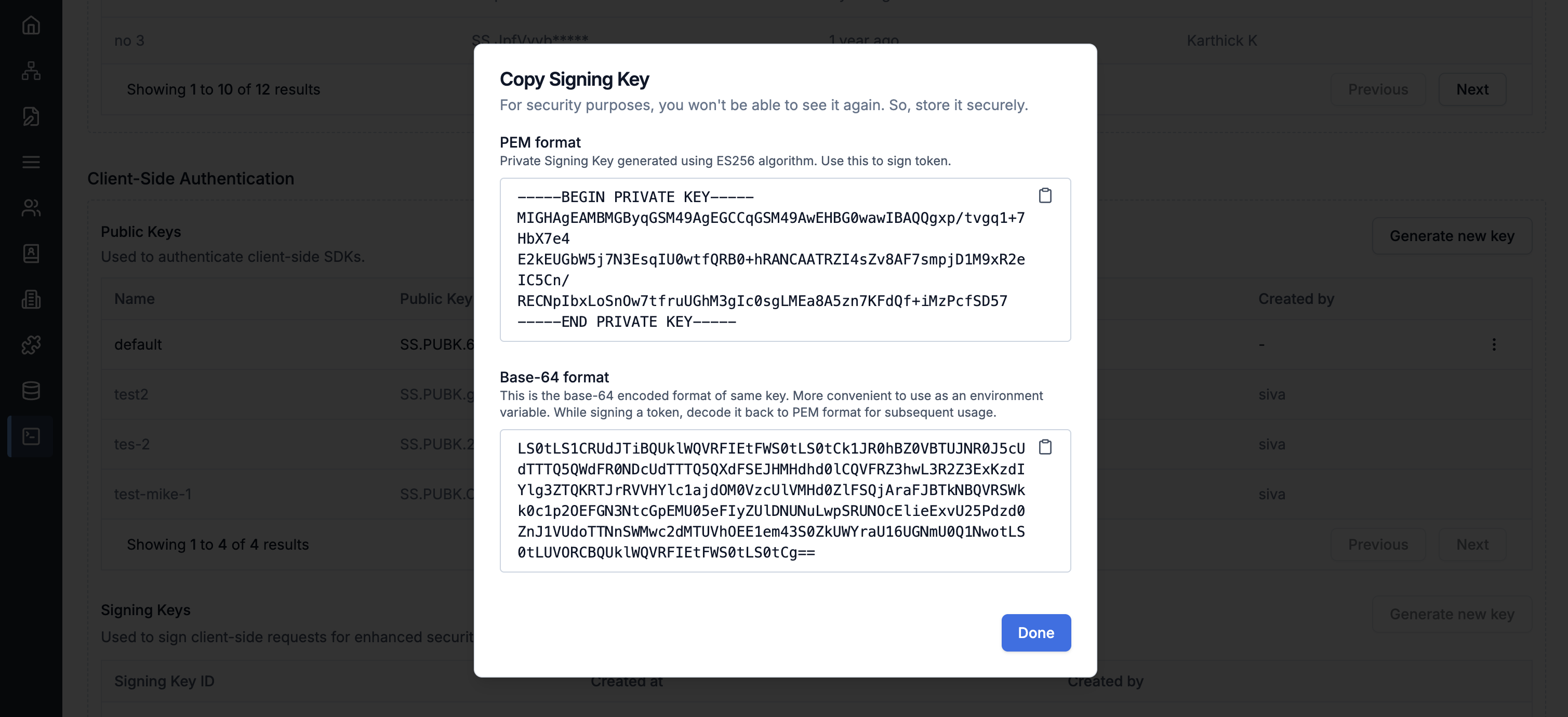

- Base64 format: This is single line text, suitable for storing as an environment variable.
- PEM format: This is multiline text format string.
Creating Signed User JWT Token
This should be created on your backend application only. You will need to sign the JWT token with the signing key from above step and expose this JWT token to your Frontend application.Create JWT token using above information:
- JWT Algorithm:ES256
- JWT Secret:Signing key in PEM format generated in step1. If you are using Base64 format, it should be converted in to PEM format.
- JWT Payload:
SuprSend requests will be scoped to tenant. If tenant passed by you in SDK doesn’t match with the JWT payload scope
tenant_id then requests will throw 403 error.If tenant_id is not passed, it is assumed to be default tenant.Currently only Inbox requests supports scope, later on we will extend it to preferences and other requests.