📘 Many of our mobile SDK’s are under revamp stage. These SDK’s still use workspace key and workspace secret authentication.
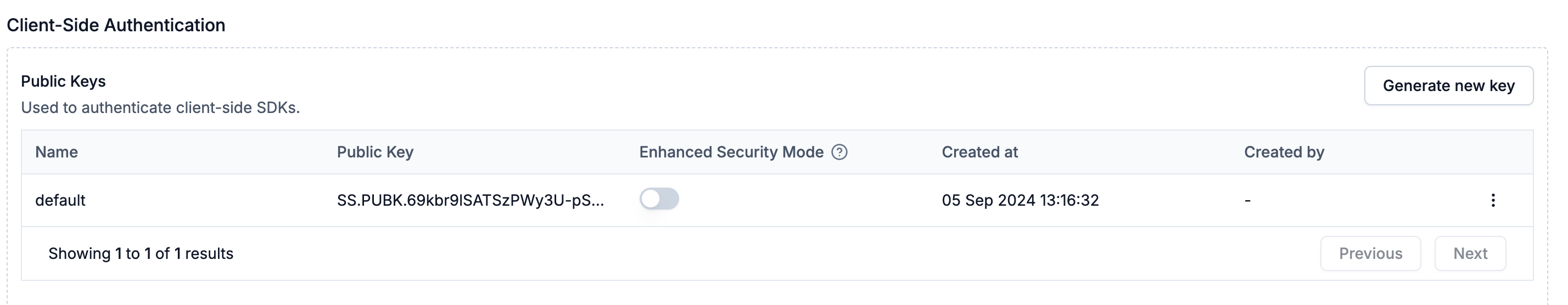
Enhanced Security Mode with signed User Token
When enhanced security mode is on, user level authentication is performed for all requests. This is recommended for Production workspaces. All requests will be rejected by SuprSend if enhanced security mode is on and signed user token is not provided. This signed user token should be generated by your backend application and should be passed to your client.Generate Signing Key
You can generate Signing key from SuprSend Dashboard (below Public Keys section in API Keys page).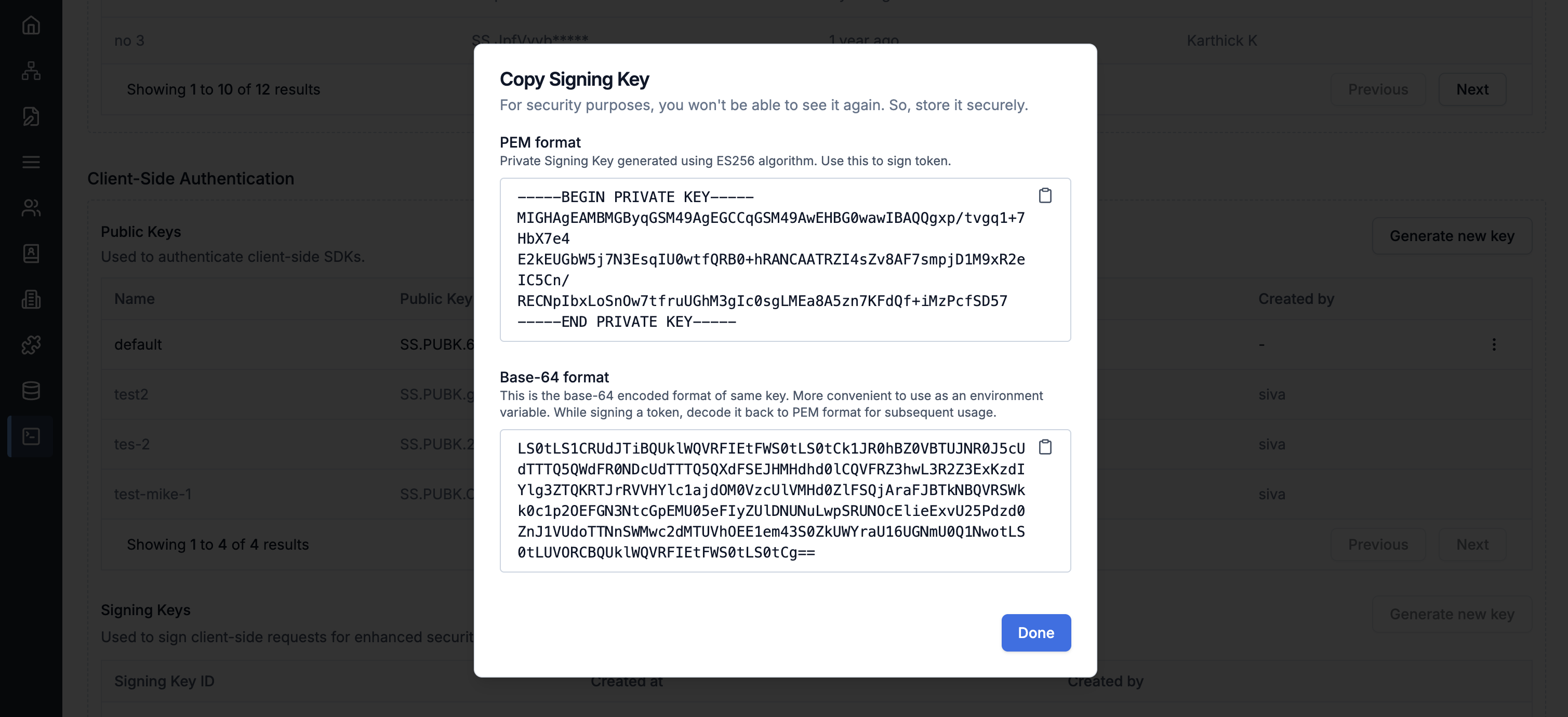

Creating Signed User JWT Token
This should be created on your backend application only. You will need to sign the JWT token with the signing key from above step and expose this JWT token to your Frontend application.Create JWT token using above information:
- JWT Algorithm:ES256
- JWT Secret:Signing key in PEM format generated in step1. If you are using Base64 format, it should be converted in to PEM format.
- JWT Payload:
SuprSend requests will be scoped to tenant. If tenant passed by you in SDK doesn’t match with the JWT payload scope
tenant_id then requests will throw 403 error.If tenant_id is not passed, it is assumed to be default tenant.Currently only Inbox requests supports scope, later on we will extend it to preferences and other requests.